Access Restrictions CIDR (IP Address) Rules
IP address access policy (CIDR Rules) for access to the Rescale platform can be configured. There are two scenarios: Per Rescale security policy, the 0.0.0.0/0 rule is blocklisted (not allowed); this includes ‘quad 0’ and derivatives. 1. Organization Level: Platform Web UI Access Policy At the organizational level, a platform administrator can define the CIDR rules to allow…
Okta SSO Setup
Step 1: Login to Okta portal with admin account Step 2: On top right click on ADMIN button Step 3: Go to Applications menu Step 4: Click on Add Application button on left side of the window Step 5: Click on Create New App Step 6: On the pop-up window, Select platform as Web and…
Workstation Administration
Monitoring Workstations in the Administrative Activity Page Workstations can be monitored through the Workspace Admin > Activity to determine how long they have been in a running or suspended state. Workstations can be Shutdown, Deleted, or Assigned to a Project from this list. Auto-Terminate Long-Suspended Workstations Administrators can auto-terminate long-suspended workstations by setting a policy…
Metadata Management Overview
Rescale Metadata Management is an advanced data management framework designed to streamline and enhance simulation data management in engineering and R&D. It provides a seamless, flexible, and automated approach for engineers to capture, manage, and utilize metadata effectively. Rescale Metadata Management supports any engineering and scientific application, ensuring broad compatibility and integration with existing systems….
NGC CUDA Quantum on Rescale
Overview In this tutorial, we will learn how to get started with NGC CUDA Quantum on the Rescale platform using the NGC Container image which contains all CUDA Quantum releases. We will use the built-in examples within the Nvidia CUDA Quantum image to demonstrate the agility, scalability and ease of use of the Rescale platform…
High Throughput Computing (HTC)
Please note that this feature is currently in beta and not enabled by default. Please contact your organization’s Solution Architect or Account Executive to enable access. Overview Rescale High Throughput Computing (HTC) is an API-based Rescale product for running a large number (e.g., hundreds to millions) of concurrent small and decoupled jobs (e.g., single-digit cores…
Cadence Innovus Tutorial
Overview In this tutorial, we will learn how to get started with Cadence Innovus software on the Rescale platform using a flat implementation flow which can be applied to chip level designs as well as blocks. We will use the block implementation Rapid Adoption Kit (RAK) from Cadence Innovus which is also available on the…
Job & Workstation Pages
Overview This page walks you through how to use and set up your Jobs and Workstation pages. In order to access the Jobs feature, log in to your Rescale account (Rescale Platform). You can create an account here if you don’t have a Rescale account. From the Job and Workstations page, you can view, manage, and configure…
Collaborating With Others By Sharing Jobs
Last updated: July 19th, 2023 Overview This page walks you through the job sharing feature, designed to foster enhanced collaboration within your team! This guide will walk you through how you can seamlessly share your running or completed jobs with others, promoting efficient knowledge sharing, team collaboration, and more productive workflows. Whether you’re sharing real-time…
Admin-Enforced Fields: Add Custom Fields To Jobs
Related: Resource Tagging: schemaless tagging for flexible categorization. Custom fields allow administrators and users to define custom fields for jobs. This feature enables greater flexibility in data capture and job management, allowing users to input job-specific information in a structured manner. There are two types of custom fields. This article will focus on Admin-Enforced fields,…
Resource Tagging
Introduction and Definitions Resource tagging is a powerful feature in Rescale that allows you to categorize and organize your resources (Jobs, Workstations, and Files) with tags. By tagging your resources, you can easily search, filter, and group items based on specific criteria, making it more efficient to manage your projects and tasks. This user guide…
Bring Your Own Software With Rescale Software Publisher (Beta) – Getting Started Guide
Overview Rescale is happy to provide Rescale Software Publisher in Beta Release. We welcome customers to try out this new capability and provide us feedback. Please contact your Rescale account team for details if you are interested. Rescale Software Publisher is a new product feature that allows organizations to bring their own software to…
Dashboard Overview
The Company Admin page Dashboard will present a summary of usage to the users. Links to Platform Admin Pages Should you require a region-specific dashboard, the following table of links will take you to each of the region-specific Admin Pages. Platform Region Dashboard link United States US Dashboard European Union EU Dashboard Japan JP Dashboard…
Economics Dashboard
Overview The Economics Dashboard gives customers a birdseye view of their monthly compute and software spending across projects and teams helping you prioritize projects and reallocate resources. It is supported at both Organization and Workspace levels. Widgets on the Economics Dashboard Charges Widget Charges widget displays the monthly total charges, software charges, and compute charges…
Compute Optimizer
Compute Optimizer is currently in Private Beta, available for any customer. If you would like access, please get in contact with your Rescale Representative. Overview Rescale’s Compute Optimizer is a feature that helps users choose the optimal hardware for their workloads, based on performance, cost, and maturity. It uses machine learning (ML) to make recommendations…
Monitoring an ANSYS Fluent Batch Job Remotely
Overview This document describes the methodology to connect and monitor a Rescale ANSYS Fluent batch job remotely using ANSYS Fluent Remote Visualization Client from a Rescale or local Workstation. Prerequisites Setup SSH connectivity in Job Settings before any jobs are submitted, as described here. A Rescale Batch and Workstation job are required to be submitted…
SSH Key Generation & SFTP
Overview This page describes the methodology of firstly generating a Secure Shell (SSH) Keypair, and secondly, how to Secure File Transfer Protocol (SFTP) into a storage device. The same method that works for STFP into a Storage Device can also be used to SFTP into a Running job (which can be useful in some scenarios)….
Elastic Cloud Workstation Overview
Rescale Elastic Cloud Workstation (ECW), known as Workstations, offer you an easy way to provide a secure, managed, cloud-based virtual engineering experience to your end users. Workstations take care of the heavy lifting of running simulations and provide a fully managed service so that you don’t have to worry about procuring, deploying, and managing a…
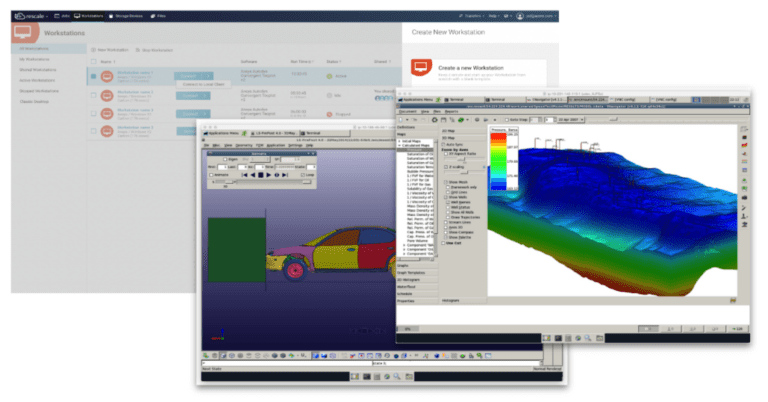
Elastic Cloud Workstations
Learn how to use Rescale Elastic Cloud Workstations, offering you an easy way to provide a secure, managed, cloud-based virtual desktop experience.